Manage Users
This section describes the basics of onboarding a user or a group of users to a Diamanti Enterprise cluster. It also describes user authentication, along with the authorization options available to users to allow access to cluster resources.
Key Terms
Term |
Description |
|---|---|
Authentication |
The user name and password-based process of finding and validating a user during cluster login. User authentication can either be local or through remote authentication providers. Currently, Diamanti supports LDAP and Active Directory-based identity providers. |
Authorization |
The process of validating user privileges against a set of Diamanti resources. While authentication validates a user’s credentials, authorization sets the permissions to access cluster resources. |
User |
An entity that is given access to a Diamanti cluster and is associated with a user name and password. The admin user is a built-in local user auto-provisioned at the time of cluster creation. |
Group |
A Diamanti object implementing authorization to Diamanti resources. A user administrator creates a local group and associates it with a set of permissions. |
Role |
A Diamanti object specifying the access rights to a resource (for ex: namespace) or to the cluster. A user administrator associates a set of roles to a local group to define the actions the group users can perform on the resource or cluster. |
Explore User Roles
Diamanti supported user roles define specific actions (edit or view) that can be performed on specific resources with appropriate scope. The dctl user role list command displays the set of Diamanti user roles, as shown in the following:
$ dctl user role list
NAME BUILT-IN SCOPE
allcontainer-edit true Cluster
allcontainer-view true Cluster
container-edit true Resource
container-view true Resource
network-edit true Cluster
network-view true Cluster
node-edit true Cluster
node-view true Cluster
perftier-edit true Cluster
perftier-view true Cluster
required true Cluster
user-edit true Cluster
user-view true Cluster
volume-edit true Cluster
volume-view true Cluster
volumeclaim-edit true Resource
For example, the admin user (created internally during cluster creation) belongs to the useradmin and cluster-admin groups, and has create, replace, update, and delete privileges to all cluster resources.
Run the dctl whoami command on the admin user to display the following:
$ dctl whoami
Name: admin
Built-In: true
Local-Auth: true
Groups: user-admin, cluster-admin
Roles: volume-edit, user-edit, allcontainer-edit, perftier-edit, network-edit, node-edit, required, container-edit/default, volumeclaim-edit/ default
Namespace: default
Login Process Overview
Before interacting with a Diamanti cluster, users need to be authenticated and authorized. Authentication is performed using either the Diamanti Enterprise Command Line Interface (CLI) or Diamanti UI.
CLI Authentication
Run the following command to initiate user authentication:
$ dctl -s cluster_IP login -u <user-name> -p <password>
You can type your short name, as shown in the following example:
$ dctl -s 172.16.19.99 login -u aduser2
Name : devtb10
Virtual IP : 172.16.19.99
Server : devtb10.eng.diamanti.com
WARNING: Thumbprint : 48 90 a6 35 4d c9 e8 f3 55 d5 45 01 83 ea 9a ee 9a da c5 27 8e e1 68 9e 88 47 b4 a8 66 1b ba 15
[CN:D10 CA 20190717010315, OU:[CA], O=[Diamanti] issued by CN:D10 CA
20190717010315, OU:[CA], O=[Diamanti]]
Configuration written successfully
Password:
Successfully logged in
Similarly, you can use your principal user name, as shown in the following example:
$ dctl -s 172.16.19.99 login -u aduser2@example.com
Name : devtb10
Virtual IP : 172.16.19.99
Server : devtb10.eng.diamanti.com
WARNING: Thumbprint : 48 90 a6 35 4d c9 e8 f3 55 d5 45 01 83 ea 9a ee 9a da c5 27 8e e1 68 9e 88 47 b4 a8 66 1b ba 15
[CN:D10 CA 20190717010315, OU:[CA], O=[Diamanti] issued by CN:D10 CA
20190717010315, OU:[CA], O=[Diamanti]]
Configuration written successfully Password:
Successfully logged in
UI Authentication
You can type your short name in the Diamanti UI to perform user authentication. The following screen appears when launching the Diamanti UI:

Similarly, you can use your principal user name in the Diamanti UI, as shown below
Onboard Users
Diamanti supports the following types of users:
Local users
Locally-managed, remotely-authenticated users
Remote users
Note that remotely-authenticated users can use their principal user name (using the username@domain format) or simply their user name (with limitations described below).
Local Users with Local Authentication
This method of onboarding users is recommended when there is a handful of users who will be accessing the Diamanti cluster directly using dctl or kubectl commands. There is no dependency on a remote identity provider (LDAP/AD).
Note: During authentication, local users with local authentication always have precedence over other types of users.
To begin, a Diamanti user administrator creates one or more groups and enables the required roles for these groups. The following example shows how to do this using the Diamanti CLI:
$ dctl user group create storage-group --role-list volume-edit
NAME BUILT-IN ROLE LIST EXTERNAL GROUP storage-group false required, volume-edit
$ dctl user create user1 --local-auth --group-list storage-group --password Diamanti@123
Name: user1
Built-In: false
Local-Auth: true
Groups: storage-group
Roles: volume-edit,required
Namespace: default
$ dctl -s 35.209.46.148 login -u user1 -p Diamanti@123
Name : shweta
Virtual IP : 35.209.46.148
Server : shweta.c.sandbox-279818.internal
WARNING: Thumbprint : 13 bf 61 21 36 00 c4 0f 54 2b cc 16 48 9f 52 b0 ac c1 6b 49 79 87 1b ae cf 3a f4 3c 26 3f 2c e6
[CN:diamanti-signer@1664876409, OU:[], O=[] issued by CN:diamanti-signer@1664876409, OU:[], O=[]]
Configuration written successfully
Successfully logged in
$ dctl whoami
Name: user1
Built-In: false
Local-Auth: true
Groups: storage-group
Roles: volume-edit, required
Namespace: default
Similarly, administrators can perform the same task using the Diamanti UI, as shown in the following:
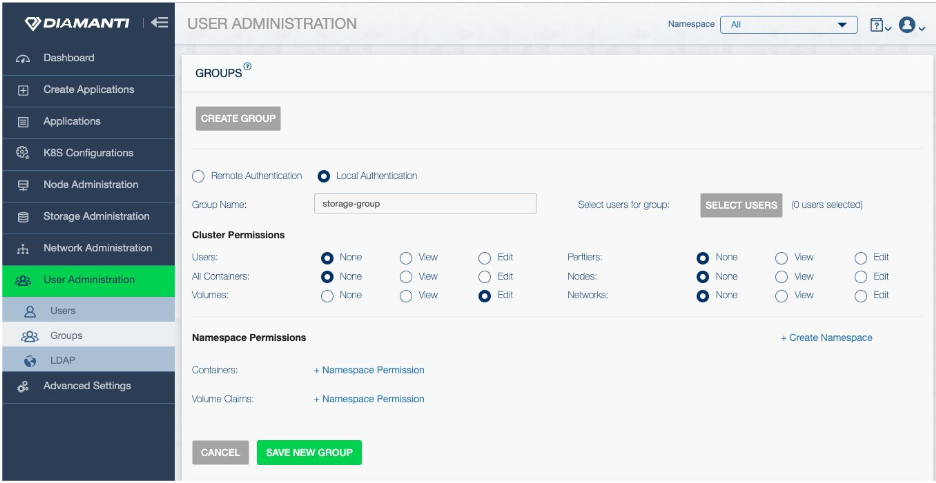
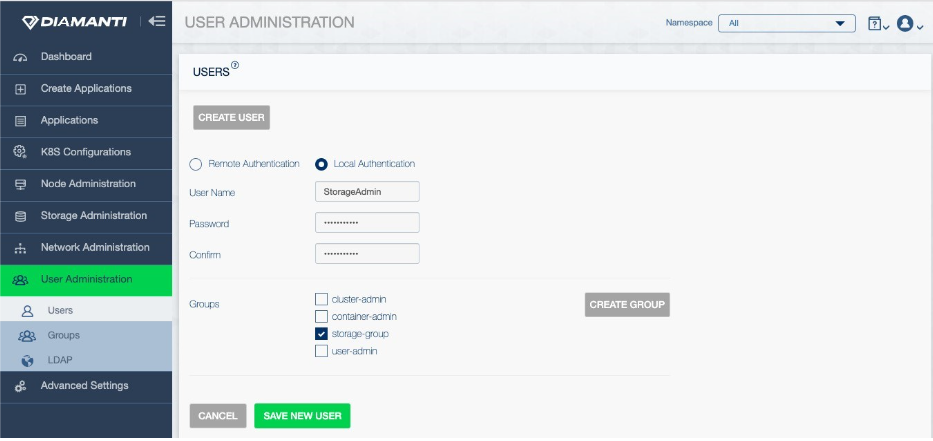
Administrators then need to add each user using either the dctl user create command or the Diamanti UI. When creating users, administrators provide a password (used for authentication) and can associate one or more groups to configure user access privileges to Diamanti resources The following shows the screen for creating and configuring users in the Diamanti UI:
Local Users with Remote Authentication
This method of onboarding users simplifies the user authentication process by not requiring a user administrator to set the password for each user created. Instead, this method relies on a remote identity provider to perform the authentication. Diamanti currently supports LDAP and Active Directory (AD) for remote authentication.
Before adding users, a user administrator first needs to configure the LDAP/AD servers used for remote authentication.
Using the command line, run the following command to configure authentication that allows administrators to specify the configuration
dctl user auth-server create [command options] [arguments...]For example,
dctl user auth-server create myauth --server ldap1.example.com --port 389 --base-dn 'dc=example,dc=com' --bind-dn 'cn=mybinddn' --bind-password 'mybindpassword' --user-filter '(sAMAccountName=%s)'
The following image shows the Diamanti UI that allows administrators to specify this configuration:
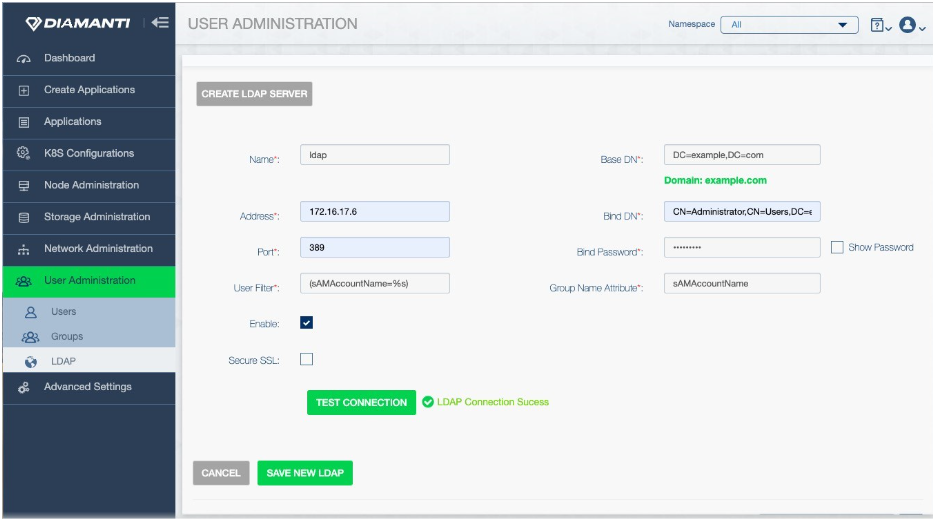
Following this, administrators only need to indicate the identity provider for authentication when creating each user, as shown in the following examples (CLI and Diamanti UI):
$ dctl user create D10Admin@adexample.com --group-list cluster-admin
Name: D10Admin@adexample.com
Built-In: false
Local-Auth: false
Groups: cluster-admin
Roles: node-edit, perftier-edit, volume-edit, required, allcontaineredit, container-edit/default, volumeclaim-edit/default, network-edit
Namespace: default
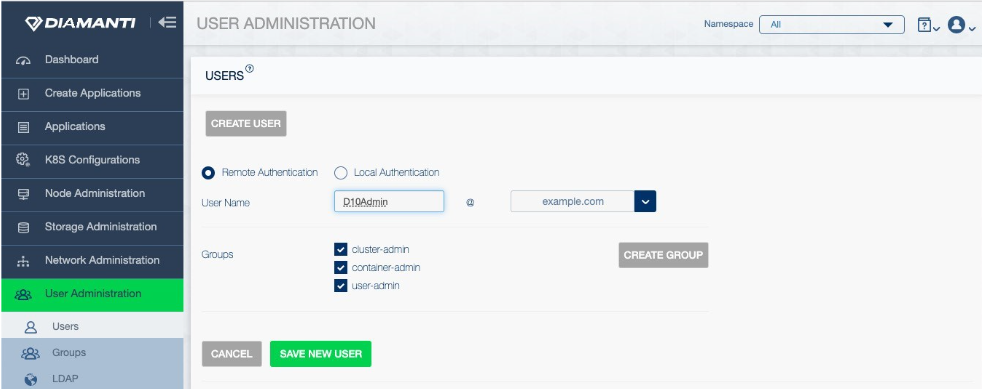
Remotely-authenticated users can use their short name or principal user name (using the username@domain format) to log in to the cluster. Note that if multiple LDAP/AD servers are configured, only the principal user name format is supported for cluster login.
Note: If the cluster was upgraded from a release prior to Diamanti v2.1.0 and auth-servers are being added to the cluster, contact Diamanti Technical Support for guidance about migrating the configuration to ensure that current users continue to be supported with the new release.
Remote Users
This method is the most convenient for managing a large number of users that might need access to the Diamanti cluster. In this scenario, user management and the corresponding authentication is entrusted to the remote identity provider.
The user administrator creates a group and associates the LDAP/AD group with this Diamanti group. This provides all users belonging to the LDAP/AD group the same privileges, as defined by the role binding for that Diamanti group.
Note
When using the dctl user-list command, remote users are not displayed but instead appear in AD or LDAP.
The following shows an example of configuring this using the CLI:
$ dctl user group create RemoteAdmins --role-list allcontainer-edit,network-edit,node-edit,perftier-edit,required,user-edit,volume-edit --external-group d10admins@example.com
NAME BUILT-IN ROLE LIST EXTERNAL GROUP
RemoteAdmins false allcontainer-edit, network-edit, node-edit, perftier-edit, required, user-edit, volume-edit d10admins@example.com
Similarly, user administrators can perform this task using the Diamanti UI:
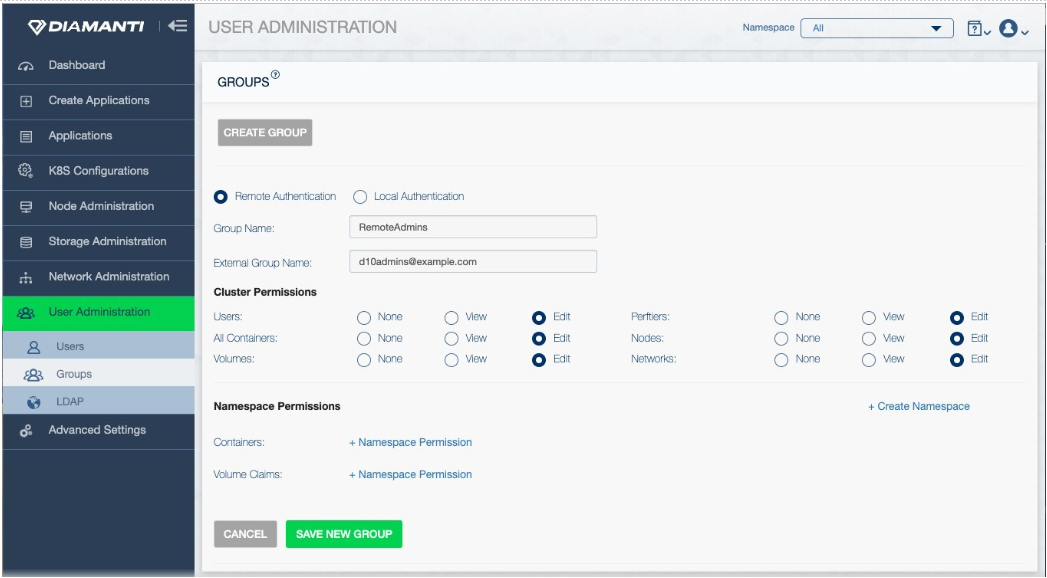
Note: Only alphanumeric characters are supported for group names created on a remote identity provider.
Remotely-authenticated users can use their short name or principal user name (using the username@domain format) to log in to the cluster. Note that if multiple LDAP/AD servers are configured, only the principal user name format is supported for cluster login.